3 Tips for implementing the NIST Cybersecurity Framework CSF
Each day more Organizations, regulators, and Governments adopt The NIST Cyber Security Framework to reduce cyber risks. The CSF is the fastest to be adopted worldwide because of its simplicity, effectiveness, and flexibility. The framework is developed to enable organizations to control cyber risks on the top management level without understanding complex security terms and skills.
Here are some tips to help you approach the implementation of the CSF in a simplified way.
The Approach:
The NIST CSF is not meant to be a checklist for compliance. Many standards define the (How & How much) in cybersecurity, including the ISO 27001, PCI-DSS, COBIT, ISA, etc. The NIST is meant to represent the “What.” The main benefit of the CSF is to make sure that Cyber Security is aligned with the organizational strategy and goals. In addition, the CSF enables executive management engagement and guides the implementation of security measures to be effective.
The CSF is Iterative
The CISO should implement the NIST Cyber Security Framework to stay alive. After its first round of implementation, it should keep evolving to take the organization through the required cybersecurity maturity levels & growth and development plans later.
Where to begin:
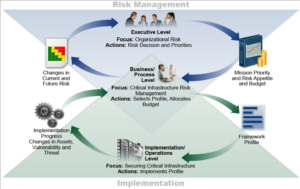
It is recommended to define first the different organization profiles. Organization Profiles include the client interface to the organization, the threats and vulnerabilities, and supplier management.
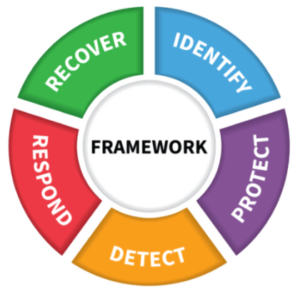
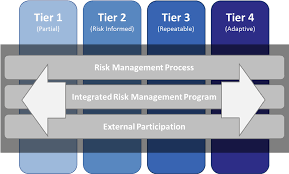
For each defined profile, the framework core is assessed to determine the tier for each category and subcategory under the CSF Core.
The list of references points to each of the subcategories’ list of standards related. This makes it easier for organizations with already implemented ISO 27001 and PCI DSS standards to manage the framework.
The tiers for each subcategory and category then determine the organization tier. Tiers are not meant to be maturity levels, so if your organization is level 3 on one of the subcategories, it might be unnecessary to adopt level 4. Some of the risks would not be significant enough for an organization to develop a level 4 considering the investment needed to reach that level.
Finally,
The CSF implementation is not a “one size fits all” approach. It is also very critical not to try to solve everything at once. Instead, the CSF implementation should spotlight the organization’s risk tolerance and enhance the C-Suit managers’ involvement in cybersecurity decision-making. The proper implementation of the framework should also help the CISO build business cases for different initiatives and guide the roadmap to cyber resilience.